출처 : https://raymii.org/s/tutorials/Keepalived-Simple-IP-failover-on-Ubuntu.html
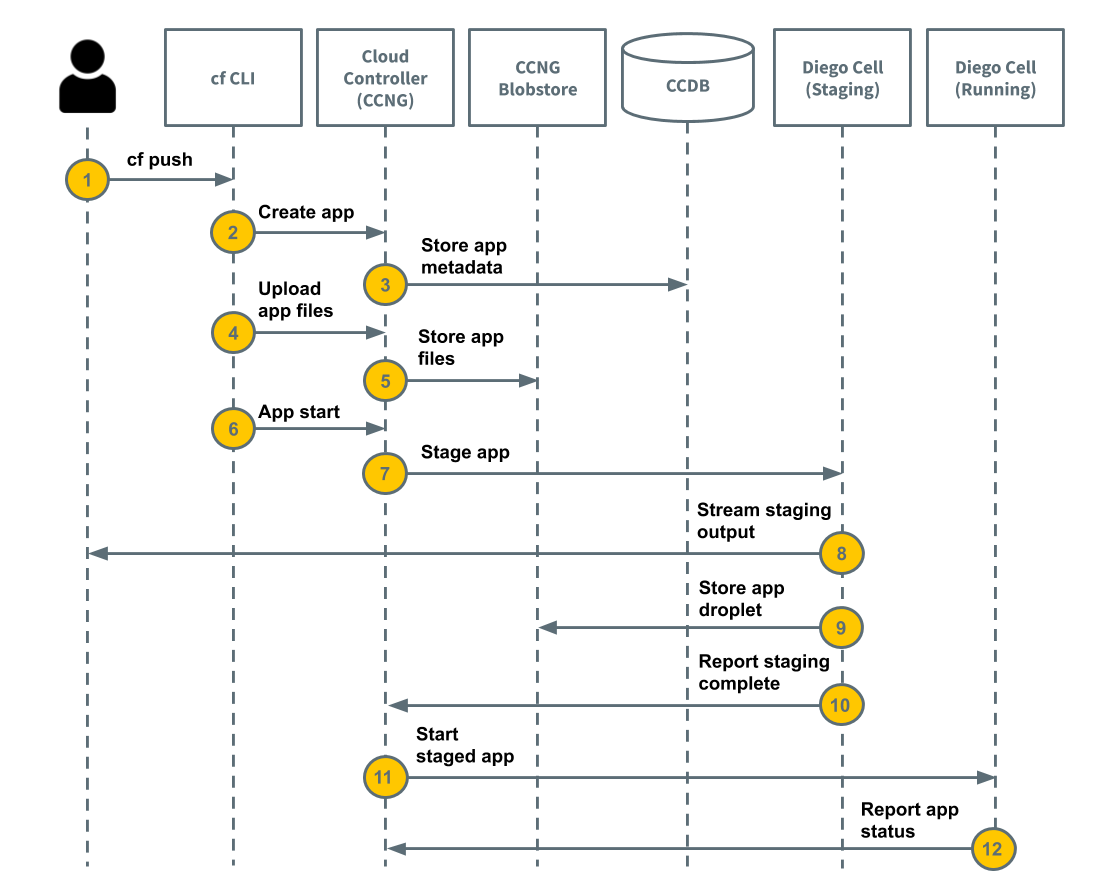
We are going to set up very simple keepalived IP failover on Ubuntu 14.04. Keepalived is a piece of software which can be used to achieve high availability by assigning two or more nodes a virtual IP and monitoring those nodes, failing over when one goes down. Keepalived can do more, like load balancing and monitoring, but this tutorial focusses on a very simple setup, just IP failover.
Internally keepalived uses VRRP. The VRRP protocol ensures that one of participating nodes is master. The backup node(s) listens for multicast packets from a node with a higher priority. If the backup node fails to receive VRRP advertisements for a period longer than three times of the advertisement timer, the backup node takes the master state and assigns the configured IP(s) to itself. In case there are more than one backup nodes with the same priority, the one with the highest IP wins the election.
I'm also a fan of Corosync/Pacemaker, you can see my articles about Corosync here.
We'll install nginx and edit the default webpage, just to see where the IP is pointing to.
Requirements
You'll need the following to get started with keepalived:
- 2 servers in the same network
I'll be using Ubuntu 14.04 servers in this example. These servers are in the 10.32.75.0/24 network. The virtual IP will be 10.32.75.200.
Install packages
Use apt to install the required packages:
apt-get install nginx keepalived
Configuring keepalived
Create the config file on the first server (10.32.75.12):
vim /etc/keepalived/keepalived.conf
Edit and paste the following config:
! Configuration File for keepalived
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 150
advert_int 1
authentication {
auth_type PASS
auth_pass $ place secure password here.
}
virtual_ipaddress {
10.32.75.200
}
}
Create the config file on the second server (10.32.75.14):
vim /etc/keepalived/keepalived.conf
Edit and paste the following config:
! Configuration File for keepalived
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass $ place secure password here.
}
virtual_ipaddress {
10.32.75.200
}
}
The priority must be highest on the server you want to be the master/primary. It can be 150 on the master, and 100, 99, 98, 97 on the slaves. The virtual_router_id must be the same on all nodes and the auth_pass must also be the same. My network configuration is on eth0, change it if yours is on another one.
Configuring NGINX
For this example I have set up a very simple NGINX server with a very simple HTML page.
vim /usr/share/nginx/html/index.html
Server 1:
<!DOCTYPE html>
<html>
<head>
<title>Keepalived 1!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Keepalived 1 - MASTER!</h1>
</body>
</html>
Server 2:
<!DOCTYPE html>
<html>
<head>
<title>Keepalived 2!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Keepalived 2 - backup!</h1>
</body>
</html>
sysctl
In order to be able to bind on a IP which is not yet defined on the system, we need to enable non local binding at the kernel level.
Temporary:
echo 1 > /proc/sys/net/ipv4/ip_nonlocal_bind
Permanent:
Add this to /etc/sysctl.conf:
net.ipv4.ip_nonlocal_bind = 1
Enable with:
sysctl -p
Start & Failover
When the website is set up we can start both NGINX and Keepalived on both servers:
service keepalived start
service nginx start
Visit the IP you configured as a failover IP in your browser. You should see the page for server 1.
Let's do a test failover. On server 1, stop keepalived:
service keepalived stop
Refresh the webpage. You should see the page for server 2. The logging will show something like this:
tail /var/log/syslog
Output:
Jun 13 22:50:59 ha2-ubu1 Keepalived_vrrp[1579]: VRRP_Instance(VI_1) Transition to MASTER STATE
Jun 13 22:51:00 ha2-ubu1 Keepalived_vrrp[1579]: VRRP_Instance(VI_1) Entering MASTER STATE
Jun 13 22:51:01 ha2-ubu1 ntpd[1445]: Listen normally on 9 eth0 10.32.75.200 UDP 123
Jun 13 22:51:01 ha2-ubu1 ntpd[1445]: peers refreshed
Jun 13 22:51:01 ha2-ubu1 ntpd[1445]: new interface(s) found: waking up resolver
As you can see, for a simple IP failover, keepalived is much simpler than corosync/pacemaker to set up.
You can read more on keepalived on their website. Another article here describes how to do load balancing with keepalived.
Tags: cluster,heartbeat,high-availability,keepalived,network,vrrp,
'나만의 Cloud' 카테고리의 다른 글
| ubuntu apache2 포트 변경 및 DocumentRoot 변경 (0) | 2016.06.02 |
|---|---|
| SLA (0) | 2016.05.09 |
| ansible 설치 및 기본 구성 (0) | 2015.08.21 |
| Virtual box Vagrant (0) | 2015.07.09 |
| puppet Resource (0) | 2014.05.19 |